Use CTI to Informed Response Actions:
To set the stage, a few years back I supported a response to a ransomware attack. The corporation in question had invested significantly in a security program, largely prompted by regulatory requirements. The security operations team was staffed by solid security engineers, as an additional duty. The organization did have a cyber threat intelligence shop that was supported by a few dedicated individuals, but the CTI was not integrated into the security operations platform. When ransomware was detected when employees could not access files on the file share.
The security operations team reached out to my company to support the incident response two days after the notification from the employee to the security team. Unfortunately the security operations team was not familiar with CTI related to ransomware attackers. As opposed to writing an indictment on their response, let's view it through the lense of how CTI on ransomware actors could inform the response activities. Here is an example flow from Cybersecurity and Infrastructure Security Agency (CISA) on the CONTI Ransomware Attack.
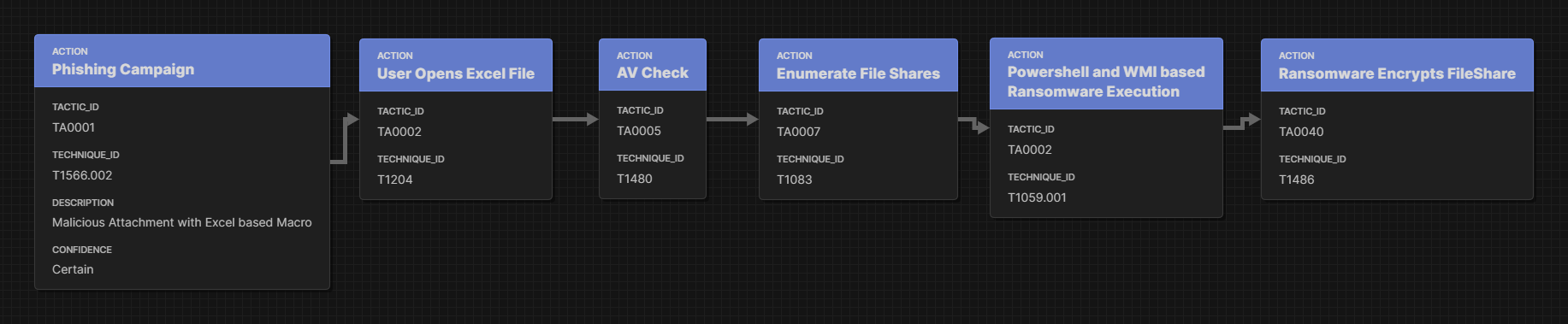
For the purposes of the article let's break the flow down into some simple steps. In this case a simple phishing campaign brought an Excel file with malicious macros that checked for particular AV/EDRs running, then scanned the mounted file shares, and executed ransomware on those available file shares.
Simplified Ransomware MITRE ATT&CK Flow
Setting aside the preventative and detection gaps on this attack let’s focus on the response. Each of the attacker’s actions in this path can provide insight into the response actions:
Phishing Campaign with Excel Macros:
Investigation: Search the Enterprise for this email by sender, attachment, or subject
Containment: Block/quarantine any suspicious messages
Attachment and AV check
Investigate: Capture the attachment and quickly open it in a sandbox for more intelligence
Investigate: Once the AV/EDR check is identified, scan the enterprise for any endpoints with or without disabled AV/EDR
Investigate: Scan the enterprise endpoints for that file
Containment: Contain/isolate any systems identified in those searches
Containment: Establish blocks (EDR and Email) for that file
File Share Enumeration:
Investigate: Search the file share and endpoint records for any other enumerations of the file share system
Containment: Possibly suspend “write” on the affected file shares
Containment: Possibly disable any accounts seen enumerating file shares
Powershell and WMI:
Investigate: Search the enterprise endpoint Powershell records
Investigate: Identify and network WMI queries across the network via RPC
Containment: Temporarily disable WMI RPC calls
Encryption:
Investigate: Search the file shares for any files with the encryption extension
Containment: Remove access to any encrypted files or folders
Containment: Stop backup process for those file shares in order not to overwrite good backups
Extraneous or Harmful actions:
Containment: Collect all laptops that reported attempted access to encrypted files
Containment: Turn off access to all file shares
Containment: Network isolate the entire file share backup process
Containment: Take down or isolate externally facing applications that have access to unaffected file stores
The desire to respond does create a sense of urgency during an incident. The decision to initiate response actions (containment and eradication) should always take two factors into account: 1) what is known about the attack and the impact of the response to the attacker (if that cannot be articulated the investigation is not mature enough) AND 2) what is the business impact of the response actions (VERSCHLIMMBESSERN).